The Zero Trust Firewall Is A Key Puzzle Piece Of A Zero Trust Architecture
Today, I'm on annual leave. Well, I was. Then I saw that Zscaler announced their intent to acquire Airgap Networks and it ruined all my plans. After first messaging everyone I knew at Zscaler to tell them how awesome this was, I quickly jumped in the car and headed home so I could put pen to paper about this.
This may strike you as a bit of an odd overreaction to a corporate acquisition (I do get a bit passionate about tech) so let me tell you a bit of a story.
Microsegmentation has been around for some time now, but it has always been hard. On the scale it has been close to impossible for two reasons - both the processing of the immense amount of network traffic as you have to see everything leaving every host, but also from a management perspective. You have to make sense of that traffic and define sensible rules so you don’t break everything, but equally, you don’t implement a flash new piece of technology and end up with the equivalent of an ANY-ANY Allow rule in place. So core to our problem statement is processing and management scalability - we will come back to this later.
I was on a call with a person I'm lucky enough to call a friend, Manoj, who is basically like the Oracle from The Matrix when it comes to this stuff. Fewer cookies (it was remote), a better sense of humour, but otherwise Oracle or sage-like. I was bemoaning the lack of solutions in this space. Cloud providers have had native micro-segmentation capability for years, but unless you have built a ground-up cloud-native application and defined your network security rulesets in code, the management just isn't there. Also, it does not account for the considerable estate that is still not in the public cloud. Ideally, we want a solution that is agnostic of the environment in which it is hosted. On-prem / Cloud. VM / HW. We want a single, manageable solution. There have been numerous attempts to solve this. Edgewise Networks (another Zscaler acquisition), had made some ground in machine learning to analyse and recommend rulesets. However, nothing had quite materialised as a broad and scalable solution. In discussing this with Manoj, he offered to introduce me to a friend of his, Ritesh Agraweal, CEO and co-founder of Airgap Networks.
 Me speaking with sage.
Me speaking with sage.
I went to have a look at their website and read their “Agentless Segmentation, Fully Managed. Deploys in hours.” claim and thought that it sounded far too good to be true. So I asked Manoj to kindly set up the introduction.
Off the back of the intro, I had a call with Ritesh in November last year (2023). I explained the above problem I wanted to solve to Ritesh, who then kindly took an hour to talk me through the Airgap solution.
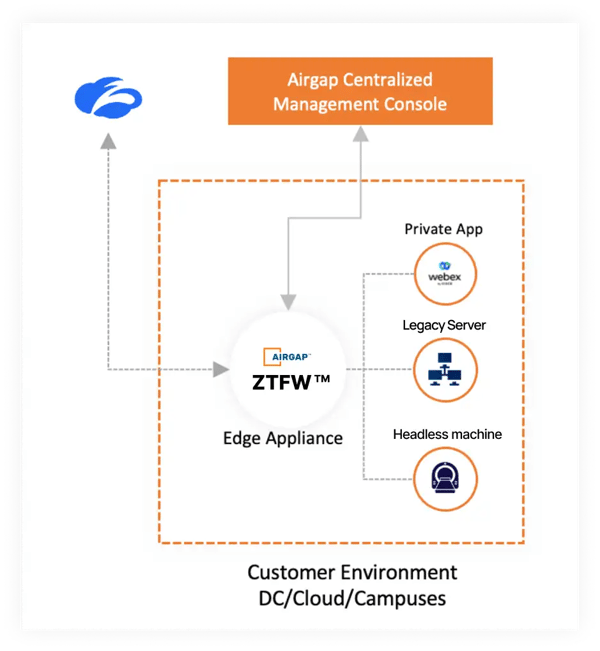
The first thing that struck me about their approach was the beauty in simplicity. It had the elegance that made me stop and think that in some ways their approach was so obvious. Rather than take an agent-based approach, or have to embed their technology at a hypervisor-type layer, Airgap operates more like an L3 tap. It works like this (I’ll use a simple example)...... you deploy an Airgap appliance into a network segment. Let's assume it's your DMZ and you have some web servers in that segment. The Airgap appliance uses the same gateway address (i.e. your firewall) as the web server does, so it has a path back to the Internet and your other internal network segments. You then proceed to change the netmask on your web servers to a /32 and the gateway to the Airgap appliance IP address. You can do this through several different means, such as a DHCP or startup script. Once you have changed the address, the traffic now routes via the Airgap appliance, which can simply sit there and learn traffic flows until you’re ready to build and enforce a policy. You can incrementally move servers into the Airgap path - there is no need to take a big-bang approach if you don’t want to. Once you have micro-segmented one network segment, you can create another VLAN/subinterface on the Airgap appliance (i.e. your database segment) and now start to update the network configurations in this segment to move traffic across to Airgap. Bit by bit traffic is no longer transiting your traditional L3 gateway/Firewall, but instead routing via Airgap. However because you aren’t changing IP addresses, everything keeps working. Eventually, you can retire your firewall. It has been replaced with what Airgap has nicely branded its Zero Trust Firewall.
These are also traffic patterns which often aren’t being seen by your SIEM or network log management today, as they aren’t transiting a firewall.
 https://airgap.io/ransomware-kill-switch
https://airgap.io/ransomware-kill-switch
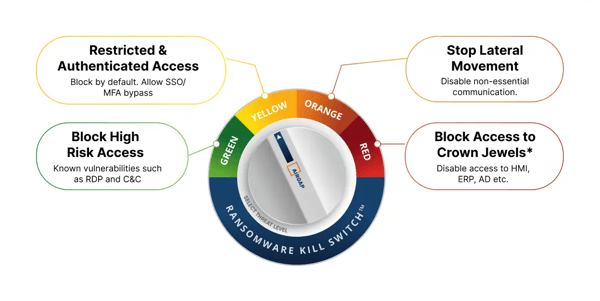
Now you could argue that you can achieve this with an existing firewall. That’s a nice idea, but if we revisit our problem statement, processing and management scalability are key. Traditional firewalls have not been built with this in mind. They have been built as a gateway in a traditional way - something you only transit when moving “zone”. If you are using /24 network segments, 254 potential host addresses can communicate with each other without transiting the gateway. With micro-segmentation, we want every packet transiting the gateway. We also then need to build a ruleset for each traffic flow. Again, with a traditional firewall, you didn’t do this. You assumed that everything within a zone or segment was essentially trusted to its peers within that network segment. This is the antithesis of a zero trust architecture - with the emphasis being on ZERO trust. While there has been some logic in grouping devices into a network segment based on similar security profiles, this is not zero trust - it is “some trust”, and we have only done this because we had no feasible alternative. Linux has had IPtables since the beginning of time, but managing it on a scale with a restrictive policy has always been challenging. This leads me to the second point on scalability. Management. A traditional firewall requires the explicit definition of rulesets. What Ritesh demonstrated to me on that call with Airgap, was its ability to learn and recommend a rule set through AI/ML analysis of traffic patterns. This allows us to manage lateral network movement in a manner we could not in the past. And that is where Airgap talks about their Ransomware Kill Switch. This is an added feature that allows you to dial up (or more so dial down) access between hosts in an instant. This is particularly useful when you have yet to fully configure your rulesets.
 https://airgap.io/ransomware-kill-switch
https://airgap.io/ransomware-kill-switch
Some of the most impactful cyber attacks in NZ’s history have spread through lateral movement on minimally segmented networks. A key value proposition with Airgap’s micro-segmentation is the ability to reduce this risk significantly, by essentially applying zero trust principles to machine-to-machine lateral traffic flow.
It is this marrying of Airgap Networks' micro-segmentation capability with Zscaler’s zero trust platform that excites me. We finally may have a solution that can put in place a key piece of the zero trust puzzle - one that I do not believe has been solved in this manner to date.
If you’re interested in reading more I’d suggest this Zscaler blog which provides an excellent rundown on the solution.
Time to go back to being kind of on leave……

12 Apr 2024




