I’m going to start this post by saying there is zero trust and then there is zero trust. What are the distinguishing factors? One is a technology concept aligned with least privileged access to connect users only to specific applications, the other is a collection of words that has marketing departments in every network company, that ever built a VPN, salivating at the opportunity to repackage decades-old technology under a new banner.
The zero trust term is being slapped across classic VPNs, 802.1x, captive portals and any other number of technologies. While they provide authentication to end-users, and can apply a set of access controls, they are still fundamentally built around users accessing networks.
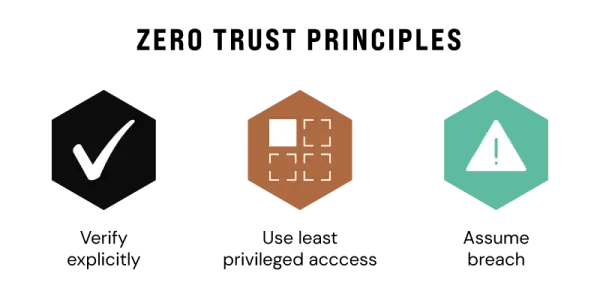
Microsoft has summed up the core principles of Zero Trust perfectly, which essentially boils down to explicitly verifying every request, using the least privileged access possible, and always assuming that a breach could have occurred. (Source: Microsoft)
However, rather than debate the nitty-gritty of network access controls, I wanted to instead focus on a more extreme view of what good looks like in the zero-trust world. We’ll call it zero trust with extreme prejudice….or ZTEP for short (and yes that is tongue in cheek).
- Firstly, ZTEP isn’t authenticated network access with a set of ACLs applied. ZTEP entirely abstracts the user away from the network layer. The network that is hosting the application that the user is connecting to should be opaque to the end device.
- ZTEP also isn’t just a port-based network restriction. Granting a user access to a particular server on port 443 can be as good as having no ACL. ZTEP needs to understand the application patterns. This includes the DNS names, ports and other indicators of an application's fingerprint.
- A full ZTEP architecture should also consider application-to-application or machine-to-machine connectivity. Why only identify users connecting to applications? Servers and applications also need to be interconnected. Some of the worst cyber attacks we have seen recently have been where lateral movement through a server network was totally unimpeded by network security controls which were only applied at layer 3 gateways, but where hundreds of hosts could communicate without ever transiting the gateway.
We make it no secret that we have a very strong relationship with Zscaler, and this really comes down to one factor. They are a market-leading security company, not a marketing company. Their acquisition game has also been absolutely on point, and rather than trying to swallow elephants, they have picked up niche technology companies that align with their zero-trust vision.
So what does zero trust with extreme prejudice architecture look like in a Zscaler world?
- Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) form the basis of your zero-trust architecture, providing role-based access to specific applications whether they are hosted internally or externally.
- Zscaler Workload Segmentation provides micro-segmentation across multi-cloud & hybrid-cloud environments. Micro-segmentation is typically hard work, and this is especially the case if you are using more than one cloud platform, but ZWS learns traffic patterns using a unique application fingerprinting engine and then helps create and define policies on how applications should be able to communicate.
- Zscaler Workload Communications connects your multi-cloud & hybrid cloud together, abstracting away from just broad network communications to ensure a policy-based approach is taken to inter-data centre traffic.
- Zscaler Deception is a relatively new offering, which as the name suggests, provides deception capabilities like decoys. Now one of the really smart things Zscaler has done with this is to bake some of the deception capabilities into Zscaler Private Access. Rather than you having to architect and deploy decoys, they are baked right into your private application access.
Ultimately, we end up with an application-aware, policy-based and least privileged access approach to traffic between our users and their applications, applications and other applications, and between our various cloud environments.
That sounds like a pretty damn good start to me. The piece I really love is how Zscaler Deception is being built into other offerings. Just when you thought you were in the circle of trust, we’re going to tempt you and test you…. sounds like something from Meet the Fockers.
That pretty much sums up the “extreme prejudice” piece for me.

23 Jun 2022




